Computers or PCs users often feel that their computers get slow. Follow these tips and you will definitely have a much faster and more reliable PC! Most of the below tips works for windows XP:
1. Wallpapers: They slow your whole system down, so if you're willing to compromise, have a basic plain one instead!
2. Drivers: Update your hardware drivers as frequently as possible. New drivers tend to increase system speed especially in the case of graphics cards, their drivers are updated by the manufacturer very frequently!
3. Minimizing: If you want to use several programs at the same time then minimize those you are not using. This helps reduce the overload on RAM.
4. Boot Faster: The 'starting Windows 95/98' message on startup can delay your booting for a couple of seconds. To get rid of this message go to c:\ and find the file Msdos.sys. Remove the Read-Only option. Next, open it in Notepad or any other text editor. Finally, go to the text 'Options' within the file and make the following changes: Add BootDelay=0. To make your booting even faster, set add Logo=0 to remove the Windows logo at startup.
5. Restart only Windows: When restarting your PC, hold down Shift to only restart Windows rather than the whole system which will only take a fraction of the time.
6. Turn Off Animations: Go to Display Settings from the Control Panel and switch to the Effects Tab. Now turn off Show Windows Content While Dragging and Smooth Edges on Screen Fonts. This tip is also helpful with Windows XP because of the various fade/scroll effects.
7. Faster Start-Menu Access: Go to the Start menu and select Run. Now type Regedit and hit Enter. The Registry Editor will appear on the screen. Now, open the folder HKEY_CURRENT_ USER\Control Panel\Desktop. You should see a MenuShowDelay value. If you don't then do the following: right click on a blank space in the right pane and select New\String. Change the name in the new value to Menu ShowDelay. Now that we have the Menu Show Delay value, double click on it and enter 0 in the value data field. This sets the start menu delay to 0 milliseconds.
8. Resolutions: If you are willing to do anything for faster performance from your PC, then try lowering your display resolution. The lower it is, the faster your PC.
9. Turn off Active Desktop: Go to your Display Properties and switch to the Web tab. Uncheck View My Active Desktop As a Web Page. Since the Active Desktop option under Windows 98 uses a lot of system resources, this option can have a dramatic effect on the speed of the whole system.
10. Defragment Often: Windows 98's Defrag tool uses Application Acceleration from Intel which means that when you defragment your drive, data is physically arranged on the drive so that applications will load faster.
11. Take your PC to Bed: Using the Advanced Power Management feature under Windows 98 gives you the option to use the sleep command. That way, you can send your PC to sleep instead of shutting it down and then restarting it. It's as simple as pressing a button and then pressing the same button to wake it up. You can tell Windows after how many minutes/hours of inactivity to automatically sleep the machine in the Advanced Power Management section of the Control Panel.
12. Faster Internet Access: If you use the Internet for reference and the sites you visit are rarely updated then try the following. In IE (the same can be done in Netscape) go to Tools, Internet Options. Next, click on Settings... In the Temporary Internet Files section. Finally, select Never for the first option and double the amount of storage space to use, click OK!
13. Benchmarking: Benchmarking can be very useful when run frequently. It can tell you how your PC's components are performing and then compare them to other machines like yours. For example, when you overclock your PC, you want to know how much more speed you have and whether it is stable. All this and more can be discovered using benchmarking. An excellent piece of software for doing this job is SiSoft Sandra which can be found in the Downloads File Archive!
14. Refresh the Taskbar without restarting: If you in some way change the taskbar, either in Regedit or elsewhere, you can refresh the task bar without restarting. Hold down Ctrl Alt Del, and double click on Explorer. Say Yes to close Explorer, but no to closing Windows. This will refresh the Taskbar and system tray.
15. Quick CD Eject: Instead of pushing the button on your drive, right-click your CD drive letter in My Computer and click on Eject. This will also remove any icons that have become associated with the CD drive.
16. Start Up Programs: Windows can be slowed down when programs run on start up. To eliminate this, check your Start up folder. You can access it from the start menu: Start, Programs, Start Up. Another way to eliminate programs from loading even before Windows actually starts is by doing the following: Click on Start, then Run. Type msconfig. It will take quite a long time for this program to load, but when you finally see it on your screen, explore the different tabs. They all have to do with how quickly your PC boots, so select what you want, and uncheck what you don't want!
17. Fonts: When Windows starts, it loads every single font in the Fonts folder. Therefore, the more fonts you have, the slower the booting process. To get rid of unwanted fonts, simply go to the Fonts folder under c:\windows and remove whatever you don't want. Fonts that have a red letter 'A' as their icon are system fonts, so don't delete them.
18. Stretching Wallpapers: Don't "stretch" your wallpaper in Windows 98 since it actually slows Windows down when you drag icons around on the desktop.
19. RAM Matters: If you have less than 32MB then you should seriously think of upgrading it to at least 64MB. Windows runs much more smoothly with 64MB or higher and tends to use less hard disk space for virtual memory.
20. Partitioning: A very nice little thing you can do to boost system performance. By partitioning your hard drive, splitting one physical drive into several logical ones, you can gain several advantages. 1. If you get a virus or you accidentally format a drive, not all will be lost. 2. By placing the swap file (Win386.swp) on a separate drive, The swap file will be less fragmented and thus, faster. 3. Place Windows on a separate drive and whenever you need to reinstall it, you rest assured that your data is safe on a separate drive. Partitioning can be done using a few programs such as FDisk which comes with DOS. However, FDisk formats everything on the hard disk before partitioning. Alternatively, you can use Partition Magic from
Power Quest to partition your hard disk without losing your data.
Goooooooogle
Loading
Introduction to Microsoft Office 2010:

Microsoft ® Office 2010 provides new forms of rich and powerful to offer their best work - whether you're at work, home or school - in a computer, Web browser, or Smartphone. It captures the attention of your audience and inspire with their ideas using improved tools, customizable templates, and photo editing capabilities. Working with several people from different places at the same exact time using new co-authoring capabilities. By offering more ways to access your files from virtually anywhere.
There are different versions of Microsoft Office uptill now. All know office 2007 and and 2003 or other have been for me personally the best office automation systems that have fulfilled many expectations and today bears his story has progressed slowly and each day has increased its different tools although many users do not use the full potential this is if you do join if different users using different tools.
Currently the public has made available a Web site where you can see what's new that you can now do within Microsoft Office 2010 with sample videos where it is not necessary to understand the language if not to:
http://www.microsoft.com/office/2010/
Ways & means - Registering a Domain or URL:
Due to internet activities, domain or website related activities are at rise. There are numerous company here and there offering different packages. On internet there are some good offers also but stop: before going first get some basic techniques are knowledge about registration of a URL or domain.
Here you start and your should know that. So lets starts from beginning as you know that in order for people to view a website, they need to enter its address, also known as its domain name or URL The characters typed into the address bar are normally a phrase that indicates something about the site be it a description, business or site name or a word that indicates the same things. The domain names offered at no cost by web hosting companies and those offered by companies which specialize in cheap domain names have a big difference between them. The domain names offered at no charge by hosting companies are not usually new domains but are in the form of a third level on their own domain names.
The free web hosting company's domain name is part of the address for a new third level domain, so you will need to type that in as well. A third level domain name is that the name is long and often tricky to recall which can be a big problem with them. Of course buying your own unique name will make the domain shorter and easier to remember. Finding a low cost one is easily possible as there are many cheap domain name companies all competing for business.
The range in price for cheap domain names varies from free to approximately seven dollars. However, if a free domain name is worth anything then it will usually be included in the price of web hosting, so in effect the customer is still paying for it. Paying for a domain name usually means that you can get it without a bundles web hosting package. You can pay anything from one dollar up for a paid for domain name.
The method of registration for a domain name makes no distinction between prices paid for the domains, so a cheap domain name is just as effective. Making sure that the domain name required is still available is usually the first thing to do. The customer must enter the name they are looking for into a certain text box and then decide on and select the extension chosen. The page will then tell them is the domain name is taken or not, if it is then they can purchase it, if not they will have to decide on a different name. Suggested alternatives will often be offered if the desired domain name is already in use.
Crooked companies sometimes make using cheap domain names a bad idea - if a person uses a crooked company then they may never actually receive their domain name. The company will tell the customer that the domain will not be active immediately and that they will have to wait for some time. Unfortunately after waiting a few days the domain is still not active, and it is no use emailing an unscrupulous company as they won't do anything.
A good first step to making sure that a person hasn't found a fraudulent company is to check with the better Business Bureau and find out if the cheap domain name company is registered. The organization that makes sure registered businesses are operating legitimately is the Better Business Bureau. Checking for traditional land based contact information such as an address and telephone number is a good second step to ensure that the cheap domain name company is not fake. Another place to check is message boards that are dedicated to webmasters, ask if anyone knows if the company has a good or bad reputation.
If no one has ever dealt with the company you may want to get alternative suggestions for a reputable company. But, if a cheap domain name company is reputable then there is not other reason the avoid getting a discounted domain name with them. A legitimate and reputable cheap domain name company is an excellent find and should be taken advantage of, the domain will work the same way no matter what was paid for it.
Here you start and your should know that. So lets starts from beginning as you know that in order for people to view a website, they need to enter its address, also known as its domain name or URL The characters typed into the address bar are normally a phrase that indicates something about the site be it a description, business or site name or a word that indicates the same things. The domain names offered at no cost by web hosting companies and those offered by companies which specialize in cheap domain names have a big difference between them. The domain names offered at no charge by hosting companies are not usually new domains but are in the form of a third level on their own domain names.
The free web hosting company's domain name is part of the address for a new third level domain, so you will need to type that in as well. A third level domain name is that the name is long and often tricky to recall which can be a big problem with them. Of course buying your own unique name will make the domain shorter and easier to remember. Finding a low cost one is easily possible as there are many cheap domain name companies all competing for business.
The range in price for cheap domain names varies from free to approximately seven dollars. However, if a free domain name is worth anything then it will usually be included in the price of web hosting, so in effect the customer is still paying for it. Paying for a domain name usually means that you can get it without a bundles web hosting package. You can pay anything from one dollar up for a paid for domain name.
The method of registration for a domain name makes no distinction between prices paid for the domains, so a cheap domain name is just as effective. Making sure that the domain name required is still available is usually the first thing to do. The customer must enter the name they are looking for into a certain text box and then decide on and select the extension chosen. The page will then tell them is the domain name is taken or not, if it is then they can purchase it, if not they will have to decide on a different name. Suggested alternatives will often be offered if the desired domain name is already in use.
Crooked companies sometimes make using cheap domain names a bad idea - if a person uses a crooked company then they may never actually receive their domain name. The company will tell the customer that the domain will not be active immediately and that they will have to wait for some time. Unfortunately after waiting a few days the domain is still not active, and it is no use emailing an unscrupulous company as they won't do anything.
A good first step to making sure that a person hasn't found a fraudulent company is to check with the better Business Bureau and find out if the cheap domain name company is registered. The organization that makes sure registered businesses are operating legitimately is the Better Business Bureau. Checking for traditional land based contact information such as an address and telephone number is a good second step to ensure that the cheap domain name company is not fake. Another place to check is message boards that are dedicated to webmasters, ask if anyone knows if the company has a good or bad reputation.
If no one has ever dealt with the company you may want to get alternative suggestions for a reputable company. But, if a cheap domain name company is reputable then there is not other reason the avoid getting a discounted domain name with them. A legitimate and reputable cheap domain name company is an excellent find and should be taken advantage of, the domain will work the same way no matter what was paid for it.
Some errors messages and their solutions:
Commone Problems with new System:
Install Norton AntiVirus was enough to boot up the machine again it is not already in Windows. Thus the problem is found quite often. May be due to our home computer users. Most will use an illegal sale is generally the IT department. Make some steps in the production of the CD is not some standard files all copies are not full. In particular, a CD disc. And dozens of program. Quite a problem, much more. When users purchase to install it as a problem to some programs such as Norton AntiVirus or prefer to go for file system extension DLL is not installed on all makes perfect. Windows can not access.
One other reason is due to drivers, sure enough. Some drivers are often a problem with the operating system and likes to meddle files. System to make Windows crash is seen then. For ways to solve problems. The computer technician. For the behavior of the user before. If found to have been installed. Or down to the driver, then boot into Windows does not make another. We assume that before that could cause the driver to program and may not be complete until the system can not start. We can solve the following problem.
To boot computer into Safe Mode because Safe Mode will sign into Windows without. Need some drivers or files. Then we go to remove the program or driver that caused the problem from a run to let the remaining carcass. Then boot into Windows computer normally.
--------------------------------------------------. ------------------------------.
PC boot up into Windows, but can not be.
If your computer through the POST process, but hold back the Windows logo screen display and could not boot into Windows at all. Sometimes do not show the Windows logo but a message comes that "Missing Operation System".
Guidelines for troubleshooting your computer is full. For the behavior of the user before use. That have been deleted some system files or empty out. Most of the problems it caused the COMMAND.COM file is corrupted or deleted file because the file COMMAND.COM to keep order within the pages of Das place as TYPE, COPY, DIR, DEL also remains. act. Contact and translation of user commands through the keyboard. And bring order to the operation. This is the file COMMAND.COM is critical operating system to be based more on Das.
How to edit is. To boot with a Startup Disk, and then print sheet command SYS C: This is a command. Copy the file into drive C: The file system will be included with the COMMAND.COM file from the computer to boot up again, this time to see how it can boot into Windows.
--------------------------------------------------. ------------------------------.
Error message 1. :. This program has performed anillegal operation and will be shut down. If the problem persists, contact the program vendor.
This suggests that some of the problems we still need to sit away the programs that install last is what the program. Try to remove it by Add / Remove Program in Control Panel after then reinstall. The changes suggest that the sheet used to install additional programs the new. Because if the old plate may be the same again. Or sometimes from the program files installed last is a problem with program files installed earlier. When reinstalling the same symptoms could be modified by updating a new version of the program.
--------------------------------------------------. ------------------------------.
Error message 2. :. Improper shut down detected, Checking disk for errore.
This problem suggests that errors in the process of Shuttle want down. May be caused by users not being shutdown method. Shuttle systems need down the problem. Resolution is to wait a few minutes, then press Esc system will become normal, so if you do not want to be like this happens again. Next time it should be how to turn off the computer by Shuttle always want first-down machine.
--------------------------------------------------. ------------------------------.
Error message 3. :. Warning Windows has detected a Registry / configuration error. Choose Safe mode to start Windows with minimal set of drivers.
This suggests that problems of errors in the Windows registry. The Windows will guide us into Safe mode to fix the problem. Troubleshooting message is quite grave risk and very pretty. Because the registry is a database of stored value and other details of the Windows. If there is a problem in this section. Require changes carefully. Otherwise it may cause the system to crash. Suggest that the problem by installing the new Windows registry to lean into a new lap old registry. Or boot with a boot disc, and then type the command Scanreg / restore, to revert to the Windows registry to back up stored last 5 days, then we choose to think that day is not a problem. Just as this can resolve the issue full (remember this post way back up important information. It before each).
--------------------------------------------------. ------------------------------.
Error messages that occurred May 4. :. Explorer has caused an error in Kermel132.dll.
This suggests that a system error file. Kernel132.dll. Users may not be able to access the Control panel has most likely occurred on the Windows Me workaround is to boot into the new machine.
Safe Mode, then follow the steps below.
1. To search files with the extension *. cpl, go find the program Search, For Files Or Folders.
2. When files found. Cpl, which were then WINDOWS \ SYSTEM. To change the name. Old individually into test files and try to see if the Control panel or. Have not changed the file back to the other. Until success. When successful, then we can know where the files that cause problems.
3. To return to change the file extensions of all files to return the same. Except file a cause. Then boot the new machine.
--------------------------------------------------. ------------------------------.
Error messages 5. :. The selected disk drive is not in use. Check to make sure a disk is inserted.
This suggests that the disk drive is not available. Please make sure to put a disc into the disc drive, and then box. For this problem may be caused by the user forgot to insert the disc into the disc drive in the box, but if it is then insert into this problem may be caused by disk or a disk drive problems. Not available to us by the disc test used with other devices, if available. This shows that a disk drive to repair or remove the new switch can solve this problem.
--------------------------------------------------. ------------------------------.
Error message 6. :. There is not enough free memory to run this program. Quit one or more programs, and try again.
This suggests that memory is not enough left in the open. To open the program and try again. The reason for that is the problem of memory or RAM is not enough of a building-block. How to solve the problem permanently (but money) is for users to install additional RAM to buy. Or is a temporary solution. While use suggest that users do not need to close down some. The only background programs running that we do not open it to use. Note from a System Tray icon area of the program is to manage to close all programs that like to eat or RAM (Resource Leak) that this program even if they quit and then still refuse to return the memory to remove Duncan. to the system. We can go check that the rest of us. How much resource by right-clicking on My Computer, then click the Performance tab, see the System Resource percentage that left few resources. If less than half, then quit and then restart a new computer program, they will return back to the same lodge.
--------------------------------------------------. ------------------------------.
Error message 7. :. Error Reading CD-ROM in Drive D:. (Or drive to a CD-ROM) Please insert CD-ROM XX With Serial Number XX in Drive d: ... if the CD-ROM is still the drive, it may require cleaning.
This error message comes up to tell that an error reading from the CD drive D: (or drive to a CD-ROM), which caused the user to press the Eject CD-ROM issue. Prior to Windows. To read successfully. How to edit is. To put the plate back to the same wait for Windows to read the finished disc is gradually brought forth. The note from the lamp to the CD-ROM drive. Should wait for the light to stop flashing before. Sometimes it may cause the user to use the CD has not been entered. CD is dirty or not as the CD drive. Can not read. Should come clean before put back to another.
--------------------------------------------------. ------------------------------.
Error message 8. : -.0x0000007B INACCESSIBLE_BOOT_DEVICE.
This error message is a notification error code number using the base as a display error. This means that the computer can not find the specified partition Limited. As the system boot partition or boot option as defined section of the Foster problem. We try to solve the system boot up again. If you still do not have a Startup boot disc, and then replaces the command Scandisk to repair.
Install Norton AntiVirus was enough to boot up the machine again it is not already in Windows. Thus the problem is found quite often. May be due to our home computer users. Most will use an illegal sale is generally the IT department. Make some steps in the production of the CD is not some standard files all copies are not full. In particular, a CD disc. And dozens of program. Quite a problem, much more. When users purchase to install it as a problem to some programs such as Norton AntiVirus or prefer to go for file system extension DLL is not installed on all makes perfect. Windows can not access.
One other reason is due to drivers, sure enough. Some drivers are often a problem with the operating system and likes to meddle files. System to make Windows crash is seen then. For ways to solve problems. The computer technician. For the behavior of the user before. If found to have been installed. Or down to the driver, then boot into Windows does not make another. We assume that before that could cause the driver to program and may not be complete until the system can not start. We can solve the following problem.
To boot computer into Safe Mode because Safe Mode will sign into Windows without. Need some drivers or files. Then we go to remove the program or driver that caused the problem from a run to let the remaining carcass. Then boot into Windows computer normally.
--------------------------------------------------. ------------------------------.
PC boot up into Windows, but can not be.
If your computer through the POST process, but hold back the Windows logo screen display and could not boot into Windows at all. Sometimes do not show the Windows logo but a message comes that "Missing Operation System".
Guidelines for troubleshooting your computer is full. For the behavior of the user before use. That have been deleted some system files or empty out. Most of the problems it caused the COMMAND.COM file is corrupted or deleted file because the file COMMAND.COM to keep order within the pages of Das place as TYPE, COPY, DIR, DEL also remains. act. Contact and translation of user commands through the keyboard. And bring order to the operation. This is the file COMMAND.COM is critical operating system to be based more on Das.
How to edit is. To boot with a Startup Disk, and then print sheet command SYS C: This is a command. Copy the file into drive C: The file system will be included with the COMMAND.COM file from the computer to boot up again, this time to see how it can boot into Windows.
--------------------------------------------------. ------------------------------.
Error message 1. :. This program has performed anillegal operation and will be shut down. If the problem persists, contact the program vendor.
This suggests that some of the problems we still need to sit away the programs that install last is what the program. Try to remove it by Add / Remove Program in Control Panel after then reinstall. The changes suggest that the sheet used to install additional programs the new. Because if the old plate may be the same again. Or sometimes from the program files installed last is a problem with program files installed earlier. When reinstalling the same symptoms could be modified by updating a new version of the program.
--------------------------------------------------. ------------------------------.
Error message 2. :. Improper shut down detected, Checking disk for errore.
This problem suggests that errors in the process of Shuttle want down. May be caused by users not being shutdown method. Shuttle systems need down the problem. Resolution is to wait a few minutes, then press Esc system will become normal, so if you do not want to be like this happens again. Next time it should be how to turn off the computer by Shuttle always want first-down machine.
--------------------------------------------------. ------------------------------.
Error message 3. :. Warning Windows has detected a Registry / configuration error. Choose Safe mode to start Windows with minimal set of drivers.
This suggests that problems of errors in the Windows registry. The Windows will guide us into Safe mode to fix the problem. Troubleshooting message is quite grave risk and very pretty. Because the registry is a database of stored value and other details of the Windows. If there is a problem in this section. Require changes carefully. Otherwise it may cause the system to crash. Suggest that the problem by installing the new Windows registry to lean into a new lap old registry. Or boot with a boot disc, and then type the command Scanreg / restore, to revert to the Windows registry to back up stored last 5 days, then we choose to think that day is not a problem. Just as this can resolve the issue full (remember this post way back up important information. It before each).
--------------------------------------------------. ------------------------------.
Error messages that occurred May 4. :. Explorer has caused an error in Kermel132.dll.
This suggests that a system error file. Kernel132.dll. Users may not be able to access the Control panel has most likely occurred on the Windows Me workaround is to boot into the new machine.
Safe Mode, then follow the steps below.
1. To search files with the extension *. cpl, go find the program Search, For Files Or Folders.
2. When files found. Cpl, which were then WINDOWS \ SYSTEM. To change the name. Old individually into test files and try to see if the Control panel or. Have not changed the file back to the other. Until success. When successful, then we can know where the files that cause problems.
3. To return to change the file extensions of all files to return the same. Except file a cause. Then boot the new machine.
--------------------------------------------------. ------------------------------.
Error messages 5. :. The selected disk drive is not in use. Check to make sure a disk is inserted.
This suggests that the disk drive is not available. Please make sure to put a disc into the disc drive, and then box. For this problem may be caused by the user forgot to insert the disc into the disc drive in the box, but if it is then insert into this problem may be caused by disk or a disk drive problems. Not available to us by the disc test used with other devices, if available. This shows that a disk drive to repair or remove the new switch can solve this problem.
--------------------------------------------------. ------------------------------.
Error message 6. :. There is not enough free memory to run this program. Quit one or more programs, and try again.
This suggests that memory is not enough left in the open. To open the program and try again. The reason for that is the problem of memory or RAM is not enough of a building-block. How to solve the problem permanently (but money) is for users to install additional RAM to buy. Or is a temporary solution. While use suggest that users do not need to close down some. The only background programs running that we do not open it to use. Note from a System Tray icon area of the program is to manage to close all programs that like to eat or RAM (Resource Leak) that this program even if they quit and then still refuse to return the memory to remove Duncan. to the system. We can go check that the rest of us. How much resource by right-clicking on My Computer, then click the Performance tab, see the System Resource percentage that left few resources. If less than half, then quit and then restart a new computer program, they will return back to the same lodge.
--------------------------------------------------. ------------------------------.
Error message 7. :. Error Reading CD-ROM in Drive D:. (Or drive to a CD-ROM) Please insert CD-ROM XX With Serial Number XX in Drive d: ... if the CD-ROM is still the drive, it may require cleaning.
This error message comes up to tell that an error reading from the CD drive D: (or drive to a CD-ROM), which caused the user to press the Eject CD-ROM issue. Prior to Windows. To read successfully. How to edit is. To put the plate back to the same wait for Windows to read the finished disc is gradually brought forth. The note from the lamp to the CD-ROM drive. Should wait for the light to stop flashing before. Sometimes it may cause the user to use the CD has not been entered. CD is dirty or not as the CD drive. Can not read. Should come clean before put back to another.
--------------------------------------------------. ------------------------------.
Error message 8. : -.0x0000007B INACCESSIBLE_BOOT_DEVICE.
This error message is a notification error code number using the base as a display error. This means that the computer can not find the specified partition Limited. As the system boot partition or boot option as defined section of the Foster problem. We try to solve the system boot up again. If you still do not have a Startup boot disc, and then replaces the command Scandisk to repair.
How to redress problems caused by Software:
Posted by
Irfan Mahmood
at
12:00 AM
|
Access to Safe Mode is another way to resolve problems. Arising from the software we have installed into it in this mode will work across the Registry, drivers, hardware and other user fees are set so step into Safe Mode boot is not damaged by these functions. therefore, should learn to use Safe Mode with it will help solve many problems. It very well. If the problem can not boot into Windows has. Will solve the problem by entering Safe Mode and then go fix that. As needed, such as if the problem is to install the driver into Safe Mode and then delete the driver is to leave. If you have problems installing programs. Have to go to Add / Remove Programs in Safe Mode and then click on the program left to create problems.
The Safe Mode can be done in the next step is to boot a new machine. Then press F8 on your keyboard emphasize other (or press and hold the Ctrl key) and then follows up menu will appear.
1.. Normal.
2. Logged (\ BOOTLOGE.TXT).
3. Safe Mode.
4. Step-by-step confirmation.
5. Command prompt only.
6. Safe modecommand promt only.
Select a topic 3 Safe Mode as we can go into Safe Mode to resolve the problems now.
The Safe Mode can be done in the next step is to boot a new machine. Then press F8 on your keyboard emphasize other (or press and hold the Ctrl key) and then follows up menu will appear.
1.. Normal.
2. Logged (\ BOOTLOGE.TXT).
3. Safe Mode.
4. Step-by-step confirmation.
5. Command prompt only.
6. Safe modecommand promt only.
Select a topic 3 Safe Mode as we can go into Safe Mode to resolve the problems now.
Toshiba portable hard drive with 320 GB and 500 GB:

An amazing invention that allows you to store data and also computer systems can easily customize the frequency, adjust the level of security
It is from Toshiba Thailand Co., Ltd. That introduces 2.5-inch hard drive, portable 320 GB capacity and 500 GB allows you to store both computer data can easily customize the frequency, adjust the level of security. And types of files saved. A security password. In addition, detection technologies in shock and preventing damage to the movement of data in the drive. Users confidence in the security of data stored on the hard drive, Toshiba. Toshiba trusted for over 20 years of manufacturing hard drives. To use all the brand name notebook computers.
For your interest is to choose c Waa New capacity 500 GB and 320 GB Price 3,790 Baht 2,650 Baht price (price including VAT) in many varied colors such as white and want mail clearly be beautiful, elegant blue, green and red dragon force ineffective. www.toshiba.co.th.
What is HUB and how it works::
Posted by
Irfan Mahmood
at
12:54 AM
|
Workings of this tool is to send signals to the entire data packet to the hub ports so that data packets received by all computers connected to the hub unless the sending computer. Sent the signal to be repeated, although the data packet has been received by the destination computer. This causes the function colossion more often when there terjadi.Misalnya delivery of data packets port A to port B and at the same time there is transmission of data packets from port C to port D, there will be collisions (collision) Because it uses the same line (line broadcast the same) so that the data packet will be corrupted causing repeated transmission of data packets. If this happens then Collison which happens to disrupt the activities of sending new data packets or replay. This resulted in a decrease of data transfer speed. Therefore, physically, hub a lamp led which indicates there collision.
When the data packet is sent through one port on hub, Then sending the data packet will be seen and sent to each port other so bandwidth on hub be divided into the port available. More port available at hub, Then bandwidth are available to be smaller for each port.
This makes the data transmission hub with many ports that are connected to the computer slows down.
When the data packet is sent through one port on hub, Then sending the data packet will be seen and sent to each port other so bandwidth on hub be divided into the port available. More port available at hub, Then bandwidth are available to be smaller for each port.
This makes the data transmission hub with many ports that are connected to the computer slows down.
Nokia New Amazing X6 Launched:
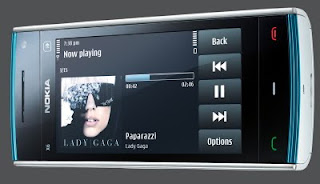
Amazing Nokia has redefined the music. It latest launched x6 and x3 the next generation music mobiles. Nokia x6 is a powerful music mobile with 3.2 inch finger touch screen, whooping 32 GB built in memory and aspect ratio of 16:9.
The music is the major attraction in this stylish gadget with continuous playback of 35 hours. A 5-megapixel camera and Carl Zeiss lens will be like camera on go. The screen was optimized for photos, videos and internet. It brings social networking communities like Face-book and allows 20 friends on virtual community called Life-casting.
Overall this device takes music in a new dimension.
Wireless Communications:
The cellular revolution is apparent in the growth of the mobile phone market. Mobile communication includes cellular personal communication systems, personal communication networks, land mobile and mobile satellite radio systems. In 1930s all mobile radio used were using amplitude modulation. In 1935, frequency modulation was used. The first generation of wireless communication is angular cellular system. The second generation of wireless communication is digital cellular system. The third generation of wireless communication is based on CDMA as the multiple access technology. Wireless network topology is the configuration in which mobile terminals communicate with another. Mobile radio transmission system may be classified as simplex, half duplex and full duplex. The important terms in wireless communication are base station, control channel, forward channel, half hand mobile station, mobile switching center, page, reverse channel, frequency division multiplexing and time division multiplexing. The examples of wireless communication are paging system, cordless telephone systems and cellular telephone systems. Some of the common wireless communication systems are TV remote control, garage door opener, paging system, cordless phone and cellular phone. A device which is capable of simultaneously transmitting and receiving operation is known as transceiver. Later on global system for mobile, digital European cordless telephone, CDMA digital cellular standard, advance mobile phone service, 3G wireless networks, Bluetooth, etc are introduced in wireless communication.
Satellite Communications:
Posted by
Irfan Mahmood
at
12:05 AM
|
Satellite communications are originally developed to provide long distance telephone service. Nowadays it has become an essential part of the world’s telecom communication system. By use of this satellite communication they serve billions of people with telephone, data as well as video services. It is also used for remote sensing like detection of water pollution, monitoring and reporting of weather conditions. In satellite service provided by satellite communication are fixed satellite service, broadcasting satellite service, mobile satellite service, navigational satellite service and meteorological satellite services. The most important satellite systems are INTELSAT, USDOMSAT AND US National Oceanographic and Atmospheric administration services of polar orbiting satellites. Geostationary orbit is an orbit in which a satellite appears to be stationary with respect to the earth. Satellite communication is classified into two segments. They are ground segment and space segment. The space segment includes tracking telemetry & command, power subsystem, attitude control system, orbital control system, thermal control system, transponders, etc. The ground segment includes stations on ship at sea, aeronautical mobile stations, home TV receives only system, commercial and military land systems. The satellite operation can be divided into two access modes. They are single access mode and multiple access modes. Recently broadcasting directly to home TV receiver using satellite is introduced which is known as Direct Broad Satellite (DBS) service.
Networks Essential:
A network is a combination of hardware and software that sends data from one location to another location. The layers of the network are higher layer, middle layer and lower layer. These layers are present in both sender section as well as receiver section. Each layer at the sending side uses the services of the layer immediately. The open system interconnection (OSI) model is the ultimate standard for data communication. The international standard organization (ISO) is a multinational body decided to worldwide agreement on international standards. The OSI model was first introduced in the late 1970s. The purpose of the OSI model is to show how to facilitate communication between different systems without requiring changes to the logic of the underlying hardware and software. It consists of seven separate but related layers. The seven layers of OSI model are physical layer, data link layer, network layer, transport layer, session layer, presentation layer and application layer. The TCP/IP protocol suite was developed prior to the OSI model. The original TCP/IP protocol suite has four layers. They are host to network layer, internet layer, transport layer and application layer. They are four types of addresses used in an internet employing. They are physical addresses, logical addresses, port addresses and specific addresses. These are the general idea about the layers of a network and its function.
Applications and Netwrok Address Translation::
Some Application Layer protocols (such as FTP and SIP) send explicit network addresses within their application data. FTP in active mode, for example, uses separate connections for control traffic (commands) and for data traffic (file contents). When requesting a file transfer, the host making the request identifies the corresponding data connection by its network layer and transport layer addresses. If the host making the request lies behind a simple NAT firewall, the translation of the IP address and/or TCP port number makes the information received by the server invalid. The Session Initiation Protocol (SIP) controls Voice over IP (VoIP) communications and suffers the same problem . SIP may use multiple ports to set up a connection and transmit voice stream via RTP. IP addresses and port numbers are encoded in the payload data and must be known prior to the traversal of NATs. Without special techniques, such as STUN, NAT behavior is unpredictable and communications may fail.
Application Layer Gateway (ALG) software or hardware may correct these problems. An ALG software module running on a NAT firewall device updates any payload data made invalid by address translation. ALGs obviously need to understand the higher-layer protocol that they need to fix, and so each protocol with this problem requires a separate ALG.
Another possible solution to this problem is to use NAT traversal techniques using protocols such as STUN or ICE or proprietary approaches in a session border controller. NAT traversal is possible in both TCP- and UDP-based applications, but the UDP-based technique is simpler, more widely understood, and more compatible with legacy NATs. In either case, the high level protocol must be designed with NAT traversal in mind, and it does not work reliably across symmetric NATs or other poorly-behaved legacy NATs.
Other possibilities are UPnP (Universal Plug and Play) or Bonjour (NAT-PMP), but these require the cooperation of the NAT device.
Most traditional client-server protocols (FTP being the main exception), however, do not send layer 3 contact information and therefore do not require any special treatment by NATs. In fact, avoiding NAT complications is practically a requirement when designing new higher-layer protocols today.
NATs can also cause problems where IPsec encryption is applied and in cases where multiple devices such as SIP phones are located behind a NAT. Phones which encrypt their signaling with IPsec encapsulate the port information within the IPsec packet meaning that NA(P)T devices cannot access and translate the port. In these cases the NA(P)T devices revert to simple NAT operation. This means that all traffic returning to the NAT will be mapped onto one client causing the service to fail. There are a couple of solutions to this problem, one is to use TLS which operates at level 4 in the OSI Reference Model and therefore does not mask the port number, or to Encapsulate the IPsec within UDP - the latter being the solution chosen by TISPAN to achieve secure NAT traversal.
The DNS protocol vulnerability announced by Dan Kaminsky on 2008 July 8 is indirectly affected by NAT port mapping. To avoid DNS server cache poisoning, it is highly desirable to not translate UDP source port numbers of outgoing DNS requests from any DNS server which is behind a firewall which implements NAT. The recommended work-around for the DNS vulnerability is to make all caching DNS servers use randomized UDP source ports. If the NAT function de-randomizes the UDP source ports, the DNS server will be made vulnerable.
Application Layer Gateway (ALG) software or hardware may correct these problems. An ALG software module running on a NAT firewall device updates any payload data made invalid by address translation. ALGs obviously need to understand the higher-layer protocol that they need to fix, and so each protocol with this problem requires a separate ALG.
Another possible solution to this problem is to use NAT traversal techniques using protocols such as STUN or ICE or proprietary approaches in a session border controller. NAT traversal is possible in both TCP- and UDP-based applications, but the UDP-based technique is simpler, more widely understood, and more compatible with legacy NATs. In either case, the high level protocol must be designed with NAT traversal in mind, and it does not work reliably across symmetric NATs or other poorly-behaved legacy NATs.
Other possibilities are UPnP (Universal Plug and Play) or Bonjour (NAT-PMP), but these require the cooperation of the NAT device.
Most traditional client-server protocols (FTP being the main exception), however, do not send layer 3 contact information and therefore do not require any special treatment by NATs. In fact, avoiding NAT complications is practically a requirement when designing new higher-layer protocols today.
NATs can also cause problems where IPsec encryption is applied and in cases where multiple devices such as SIP phones are located behind a NAT. Phones which encrypt their signaling with IPsec encapsulate the port information within the IPsec packet meaning that NA(P)T devices cannot access and translate the port. In these cases the NA(P)T devices revert to simple NAT operation. This means that all traffic returning to the NAT will be mapped onto one client causing the service to fail. There are a couple of solutions to this problem, one is to use TLS which operates at level 4 in the OSI Reference Model and therefore does not mask the port number, or to Encapsulate the IPsec within UDP - the latter being the solution chosen by TISPAN to achieve secure NAT traversal.
The DNS protocol vulnerability announced by Dan Kaminsky on 2008 July 8 is indirectly affected by NAT port mapping. To avoid DNS server cache poisoning, it is highly desirable to not translate UDP source port numbers of outgoing DNS requests from any DNS server which is behind a firewall which implements NAT. The recommended work-around for the DNS vulnerability is to make all caching DNS servers use randomized UDP source ports. If the NAT function de-randomizes the UDP source ports, the DNS server will be made vulnerable.
Network Address Translation (NAT):
Posted by
Irfan Mahmood
at
7:30 PM
|
In computer networking, network address translation (NAT) is the process of modifying network address information in datagram packet headers while in transit across a traffic routing device for the purpose of remapping a given address space into another.
Most often today, NAT is used in conjunction with network masquerading (or IP masquerading) which is a technique that hides an entire address space, usually consisting of private network addresses (RFC 1918), behind a single IP address in another, often public address space. This mechanism is implemented in a routing device that uses stateful translation tables to map the "hidden" addresses into a single address and then rewrites the outgoing Internet Protocol (IP) packets on exit so that they appear to originate from the router. In the reverse communications path, responses are mapped back to the originating IP address using the rules ("state") stored in the translation tables. The translation table rules established in this fashion are flushed after a short period without new traffic refreshing their state.
As described, the method only allows transit traffic through the router when it is originating in the masqueraded network, since this establishes the translation tables. However, most NAT devices today allow the network administrator to configure translation tables entries for permanent use. This feature is often referred to as "static NAT" or port forwarding and allows traffic originating in the 'outside' network to reach designated hosts in the masqueraded network.
Because of the popularity of this technique, see below, the term NAT has become virtually synonymous with the method of IP masquerading.
Network address translation has serious consequences (see below, Drawbacks & Benefits) on the quality of Internet connectivity and requires careful attention to the details of its implementation. As a result, many methods have been devised to alleviate the issues encountered. See article on NAT traversal.
Most often today, NAT is used in conjunction with network masquerading (or IP masquerading) which is a technique that hides an entire address space, usually consisting of private network addresses (RFC 1918), behind a single IP address in another, often public address space. This mechanism is implemented in a routing device that uses stateful translation tables to map the "hidden" addresses into a single address and then rewrites the outgoing Internet Protocol (IP) packets on exit so that they appear to originate from the router. In the reverse communications path, responses are mapped back to the originating IP address using the rules ("state") stored in the translation tables. The translation table rules established in this fashion are flushed after a short period without new traffic refreshing their state.
As described, the method only allows transit traffic through the router when it is originating in the masqueraded network, since this establishes the translation tables. However, most NAT devices today allow the network administrator to configure translation tables entries for permanent use. This feature is often referred to as "static NAT" or port forwarding and allows traffic originating in the 'outside' network to reach designated hosts in the masqueraded network.
Because of the popularity of this technique, see below, the term NAT has become virtually synonymous with the method of IP masquerading.
Network address translation has serious consequences (see below, Drawbacks & Benefits) on the quality of Internet connectivity and requires careful attention to the details of its implementation. As a result, many methods have been devised to alleviate the issues encountered. See article on NAT traversal.
Some Questions and their Answer:
What is Broadband Internet Access?The term broadband refers to any type of transmission technique that carries several data channels over a common wire. DSL service, for example, combines separate voice and data channels over a single telephone line. In DSL, voice fills the low end of the frequency spectrum and data fills the high end.
In home networking, broadband constitutes any form of high-speed Internet access using this transmission technique. Both DSL and cable modem are common broadband Internet technologies. So-called broadband
The term "broadband" refers to a communications technique for transmitting multiple simultaneous data channels. Broadband is a popular form of high-speed Internet access.
What is Dial Up Internet Access?
Dial up networking technology provides PCs and other network devices access to a LAN or WAN via standard telephone lines. Dial up Internet service providers offer subscription plans for home computer users.
Types of dial up services include V.34 and V.90 modem as well as Integrated Services Digital Network (ISDN). Dial up systems utilize special-purpose network protocols like Point-to-Point Protocol (PPP).
To use a dial up Internet connection, a client modem calls another modem located at the Internet Service Provider (ISP). The modems transfer network information over the telephone until one modem or the other disconnects.
When the popularity of the Internet exploded in the 1990s, dial up was the most common form of Internet access due mainly to its low cost to setup. However, the performance of dial up networking is relatively poor due to the limitations of traditional modem technology. V.90 modem dial up supports less than 56 Kbps bandwidth and ISDN handles approximately 128Kbps.
Many home users are currently replacing their dial up services with high-speed broadband technologies that operate at much higher speeds.
Dial up networking technology provides PCs and other network devices access to a LAN or WAN via telephone lines. Dial up Internet service providers offer subscription plans for home computer users.
What is Satellite Internet Access?
Satellite Internet is a form of high-speed Internet service. Satellite Internet services utilize telecommunications satellites in Earth orbit to provide Internet access to consumers.
Satellite Internet service covers areas where DSL and cable access is unavailable. Satellite offers less network bandwidth compared to DSL or cable, however. In addition, the long delays required to transmit data between the satellite and the ground stations tend to create high network latency, causing a sluggish performance experience in some cases. Network applications like VPN and online gaming may not function properly over satellite Internet connections due to these latency issues.
Older residential satellite Internet services supported only "one-way" downloads over the satellite link, requiring a telephone modem for uploading. All newer satellite services support full "two-way" satellite links.
Satellite Internet service does not necessary utilitize WiMax. WiMax technology supplies one method to deliver high-speed Internet service over wireless links, but satellite providers may implement their systems differently
Satellite Internet is a form of high-speed Internet service. Satellite Internet utilizes telecommunications satellites in Earth orbit to provide wireless Internet access to consumers. Satellite Internet covers many areas where DSL and cable services are unavailable.
What is Integrated Services Digital Network:
ISDN is a network technology that supports digital transfer of simultaneous voice and data traffic. Similar to DSL in this respect, an ISDN Internet service works over ordinary telephone lines. ISDN Internet service generally supports data rates of 128 Kbps.
ISDN emerged as an alternative to traditional dialup networking during the 1990s. The relatively high cost of ISDN service, though, limited its popularity with residential customers at the outset. More recently, the much higher network speeds supported by newer broadband technologies like DSL have drawn many consumers away from ISDN service.
ISDN technology today has limited applications as a networking solution. Some customers who live in rural areas of the U.S. subscribe to ISDN Internet as an alternative to satellite Internet. ISDN phone service also remains fairly common in some European countries.
ISDN supports simultaneous voice and data network connectivity over ordinary telephone lines. ISDN emerged as an alternative to traditional dial-up networking during the 1990s, but more recently its popularity has waned.
What is a Default Gateway?
You will sometimes see the term default gateway on network configuration screens in Microsoft Windows.
Answer: In computer networking, a default gateway is the device that passes traffic from the local subnet to devices on other subnets. The default gateway often connects a local network to the Internet, although internal gateways for local networks also exist.
Internet default gateways are typically one of two types:
On home or small business networks with a broadband router to share the Internet connection, the home router serves as the default gateway.
On home or small business networks without a router, such as for residences with dialup Internet access, a router at the Internet Service Provider location serves as the default gateway.
Default network gateways can also be configured using an ordinary computer instead of a router. These gateways use two network adapters, one connected to the local subnet and one to the outside network. Either routers or gateway computers can be used to network local subnets such as those in larger businesses.
In Microsoft Windows, the IP address of a computer's default gateway can be accessed in the 'ipconfig' or 'winipcfg' utilities
In computer networking, a default gateway is the device that passes traffic from the local subnet to devices on other subnets. On home networks, the router serves as the default gateway. (Courtesy by www.about.com)
In home networking, broadband constitutes any form of high-speed Internet access using this transmission technique. Both DSL and cable modem are common broadband Internet technologies. So-called broadband
The term "broadband" refers to a communications technique for transmitting multiple simultaneous data channels. Broadband is a popular form of high-speed Internet access.
What is Dial Up Internet Access?
Dial up networking technology provides PCs and other network devices access to a LAN or WAN via standard telephone lines. Dial up Internet service providers offer subscription plans for home computer users.
Types of dial up services include V.34 and V.90 modem as well as Integrated Services Digital Network (ISDN). Dial up systems utilize special-purpose network protocols like Point-to-Point Protocol (PPP).
To use a dial up Internet connection, a client modem calls another modem located at the Internet Service Provider (ISP). The modems transfer network information over the telephone until one modem or the other disconnects.
When the popularity of the Internet exploded in the 1990s, dial up was the most common form of Internet access due mainly to its low cost to setup. However, the performance of dial up networking is relatively poor due to the limitations of traditional modem technology. V.90 modem dial up supports less than 56 Kbps bandwidth and ISDN handles approximately 128Kbps.
Many home users are currently replacing their dial up services with high-speed broadband technologies that operate at much higher speeds.
Dial up networking technology provides PCs and other network devices access to a LAN or WAN via telephone lines. Dial up Internet service providers offer subscription plans for home computer users.
What is Satellite Internet Access?
Satellite Internet is a form of high-speed Internet service. Satellite Internet services utilize telecommunications satellites in Earth orbit to provide Internet access to consumers.
Satellite Internet service covers areas where DSL and cable access is unavailable. Satellite offers less network bandwidth compared to DSL or cable, however. In addition, the long delays required to transmit data between the satellite and the ground stations tend to create high network latency, causing a sluggish performance experience in some cases. Network applications like VPN and online gaming may not function properly over satellite Internet connections due to these latency issues.
Older residential satellite Internet services supported only "one-way" downloads over the satellite link, requiring a telephone modem for uploading. All newer satellite services support full "two-way" satellite links.
Satellite Internet service does not necessary utilitize WiMax. WiMax technology supplies one method to deliver high-speed Internet service over wireless links, but satellite providers may implement their systems differently
Satellite Internet is a form of high-speed Internet service. Satellite Internet utilizes telecommunications satellites in Earth orbit to provide wireless Internet access to consumers. Satellite Internet covers many areas where DSL and cable services are unavailable.
What is Integrated Services Digital Network:
ISDN is a network technology that supports digital transfer of simultaneous voice and data traffic. Similar to DSL in this respect, an ISDN Internet service works over ordinary telephone lines. ISDN Internet service generally supports data rates of 128 Kbps.
ISDN emerged as an alternative to traditional dialup networking during the 1990s. The relatively high cost of ISDN service, though, limited its popularity with residential customers at the outset. More recently, the much higher network speeds supported by newer broadband technologies like DSL have drawn many consumers away from ISDN service.
ISDN technology today has limited applications as a networking solution. Some customers who live in rural areas of the U.S. subscribe to ISDN Internet as an alternative to satellite Internet. ISDN phone service also remains fairly common in some European countries.
ISDN supports simultaneous voice and data network connectivity over ordinary telephone lines. ISDN emerged as an alternative to traditional dial-up networking during the 1990s, but more recently its popularity has waned.
What is a Default Gateway?
You will sometimes see the term default gateway on network configuration screens in Microsoft Windows.
Answer: In computer networking, a default gateway is the device that passes traffic from the local subnet to devices on other subnets. The default gateway often connects a local network to the Internet, although internal gateways for local networks also exist.
Internet default gateways are typically one of two types:
On home or small business networks with a broadband router to share the Internet connection, the home router serves as the default gateway.
On home or small business networks without a router, such as for residences with dialup Internet access, a router at the Internet Service Provider location serves as the default gateway.
Default network gateways can also be configured using an ordinary computer instead of a router. These gateways use two network adapters, one connected to the local subnet and one to the outside network. Either routers or gateway computers can be used to network local subnets such as those in larger businesses.
In Microsoft Windows, the IP address of a computer's default gateway can be accessed in the 'ipconfig' or 'winipcfg' utilities
In computer networking, a default gateway is the device that passes traffic from the local subnet to devices on other subnets. On home networks, the router serves as the default gateway. (Courtesy by www.about.com)
Networking Security – A Start for Beginner::
Posted by
Irfan Mahmood
at
7:27 AM
|
An Introduction to the Key Security Issues for the E-Business Economy
With the explosion of the public Internet and e-commerce, private computers, and computer networks, if not adequately secured, are increasingly vulnerable to damaging attacks. Hackers, viruses, vindictive employees and even human error all represent clear and present dangers to networks. And all computer users, from the most casual Internet surfers to large enterprises, could be affected by network security breaches. However, security breaches can often be easily prevented. How? This guide provides you with a general overview of the most common network security threats and the steps you and your organization can take to protect yourselves from threats and ensure that the data traveling across your networks is safe.
Importance of Security
The Internet has undoubtedly become the largest public data network, enabling and facilitating both personal and business communications worldwide. The volume of traffic moving over the Internet, as well as corporate networks, is expanding exponentially every day. More and more communication is taking place via e-mail; mobile workers, telecommuters, and branch offices are using the Internet to remotely connect to their corporate networks; and commercial transactions completed over the Internet, via the World Wide Web, now account for large portions of corporate revenue.
With the explosion of the public Internet and e-commerce, private computers, and computer networks, if not adequately secured, are increasingly vulnerable to damaging attacks. Hackers, viruses, vindictive employees and even human error all represent clear and present dangers to networks. And all computer users, from the most casual Internet surfers to large enterprises, could be affected by network security breaches. However, security breaches can often be easily prevented. How? This guide provides you with a general overview of the most common network security threats and the steps you and your organization can take to protect yourselves from threats and ensure that the data traveling across your networks is safe.
Importance of Security
The Internet has undoubtedly become the largest public data network, enabling and facilitating both personal and business communications worldwide. The volume of traffic moving over the Internet, as well as corporate networks, is expanding exponentially every day. More and more communication is taking place via e-mail; mobile workers, telecommuters, and branch offices are using the Internet to remotely connect to their corporate networks; and commercial transactions completed over the Internet, via the World Wide Web, now account for large portions of corporate revenue.
Subscribe to:
Posts (Atom)